Pentesting Report Template
Pentesting Report Template - Penetration tests usually simulate a variety of attacks that could threaten a business. There are different types of penetration testing, depending upon the goal of the organization which include: They can examine whether a system is robust enough to withstand attacks from authenticated and. It involves a methodical process where cybersecurity. You’ll learn about the different types of penetration tests, why it’s critical, how the process works, and what exactly an attacker is thinking or trying to achieve during an engagement. Enhance your security posture with cobalt's fast and scalable penetration testing services, backed by a team of 450+ experts to identify and remediate vulnerabilities effectively. The purpose of this simulated attack is. Watch this webinar to learn how to get the most out of your penetration test and what to expect from a penetration test. These vulnerabilities may exist in operating systems,. Discover the types of penetration tests: Penetration testers are security professionals skilled in the art of ethical hacking, which is the use of hacking tools and techniques to fix security weaknesses rather than cause. You’ll learn about the different types of penetration tests, why it’s critical, how the process works, and what exactly an attacker is thinking or trying to achieve during an engagement. Penetration testing, aka pen testing or ethical hacking, attempts to breach a system's security for the purpose of vulnerability identification. In the context of web application. Choose v3 (new version) for the latest. Enhance your security posture with cobalt's fast and scalable penetration testing services, backed by a team of 450+ experts to identify and remediate vulnerabilities effectively. Understanding penetration testing in cyber security at its core, penetration testing (a.k.a., pentesting) is a simulation. In most cases, both humans and automated. Watch this webinar to learn how to get the most out of your penetration test and what to expect from a penetration test. There are different types of penetration testing, depending upon the goal of the organization which include: You’ll learn about the different types of penetration tests, why it’s critical, how the process works, and what exactly an attacker is thinking or trying to achieve during an engagement. A penetration test, also known as a pen test, is a simulated cyber attack against your computer system to check for exploitable vulnerabilities. They can examine whether a system is. It’s designed to replicate the creativity and persistence of real. It involves a methodical process where cybersecurity. Discover our certifications pentest+ pentest+ comptia pentest+ is the most comprehensive certification covering all penetration testing stages. Black box, grey box, and white box. Penetration tests usually simulate a variety of attacks that could threaten a business. Penetration testers are security professionals skilled in the art of ethical hacking, which is the use of hacking tools and techniques to fix security weaknesses rather than cause. Discover our certifications pentest+ pentest+ comptia pentest+ is the most comprehensive certification covering all penetration testing stages. Penetration testing (pen testing) is a simulated cyberattack designed to identify security vulnerabilities and test. You’ll learn about the different types of penetration tests, why it’s critical, how the process works, and what exactly an attacker is thinking or trying to achieve during an engagement. Black box, grey box, and white box. Choose v3 (new version) for the latest. Penetration testing, aka pen testing or ethical hacking, attempts to breach a system's security for the. Penetration testing is a form of ethical hacking. Discover the types of penetration tests: Penetration testers are security professionals skilled in the art of ethical hacking, which is the use of hacking tools and techniques to fix security weaknesses rather than cause. Penetration testing, also known as pen testing or ethical hacking, is a systematic process of testing computer systems,. Penetration tests usually simulate a variety of attacks that could threaten a business. Penetration testing, also known as pen testing or ethical hacking, is a systematic process of testing computer systems, networks, and applications to find security weaknesses. A penetration test, also known as a pen test, is a simulated cyber attack against your computer system to check for exploitable. In most cases, both humans and automated. Penetration testers are security professionals skilled in the art of ethical hacking, which is the use of hacking tools and techniques to fix security weaknesses rather than cause. Reporting helps you patch them before true hackers. Network (external and internal), wireless, web application, social engineering,. Penetration testing, aka pen testing or ethical hacking,. Evaluate the security of your infrastructure with reliable testing methods. Pentesting (penetration testing) is a simulated cyber attack conducted to identify security vulnerabilities in a system, network, or application and assess its resilience against. Black box, grey box, and white box. Discover the types of penetration tests: Penetration testing is a form of ethical hacking. Network (external and internal), wireless, web application, social engineering,. A penetration test, also known as a pen test, is a simulated cyber attack against your computer system to check for exploitable vulnerabilities. Penetration testing, aka pen testing or ethical hacking, attempts to breach a system's security for the purpose of vulnerability identification. Penetration tests usually simulate a variety of attacks. A penetration test, also known as a pen test, is a simulated cyber attack against your computer system to check for exploitable vulnerabilities. Penetration testing, or pen testing, is an attempt to evaluate the security of an it infrastructure by safely trying to exploit vulnerabilities. Penetration testing is a form of ethical hacking. It’s designed to replicate the creativity and. Penetration testing, or pen testing, is an attempt to evaluate the security of an it infrastructure by safely trying to exploit vulnerabilities. Network (external and internal), wireless, web application, social engineering,. Discover the types of penetration tests: You’ll learn about the different types of penetration tests, why it’s critical, how the process works, and what exactly an attacker is thinking or trying to achieve during an engagement. In the context of web application. Reporting helps you patch them before true hackers. There are different types of penetration testing, depending upon the goal of the organization which include: Discover our certifications pentest+ pentest+ comptia pentest+ is the most comprehensive certification covering all penetration testing stages. The purpose of this simulated attack is. Introduction to penetration testing definition and purpose penetration testing, or pen testing, is the process of simulating cyberattacks on a system, network, or application to. In this guide, we'll explore the fundamentals of penetration testing, its importance in cybersecurity, and how it fits into the software development lifecycle (sdlc). Penetration testing, aka pen testing or ethical hacking, attempts to breach a system's security for the purpose of vulnerability identification. Penetration tests usually simulate a variety of attacks that could threaten a business. Watch this webinar to learn how to get the most out of your penetration test and what to expect from a penetration test. Penetration testers are security professionals skilled in the art of ethical hacking, which is the use of hacking tools and techniques to fix security weaknesses rather than cause. Evaluate the security of your infrastructure with reliable testing methods.Pentesting Report PDF Test Data Transmission
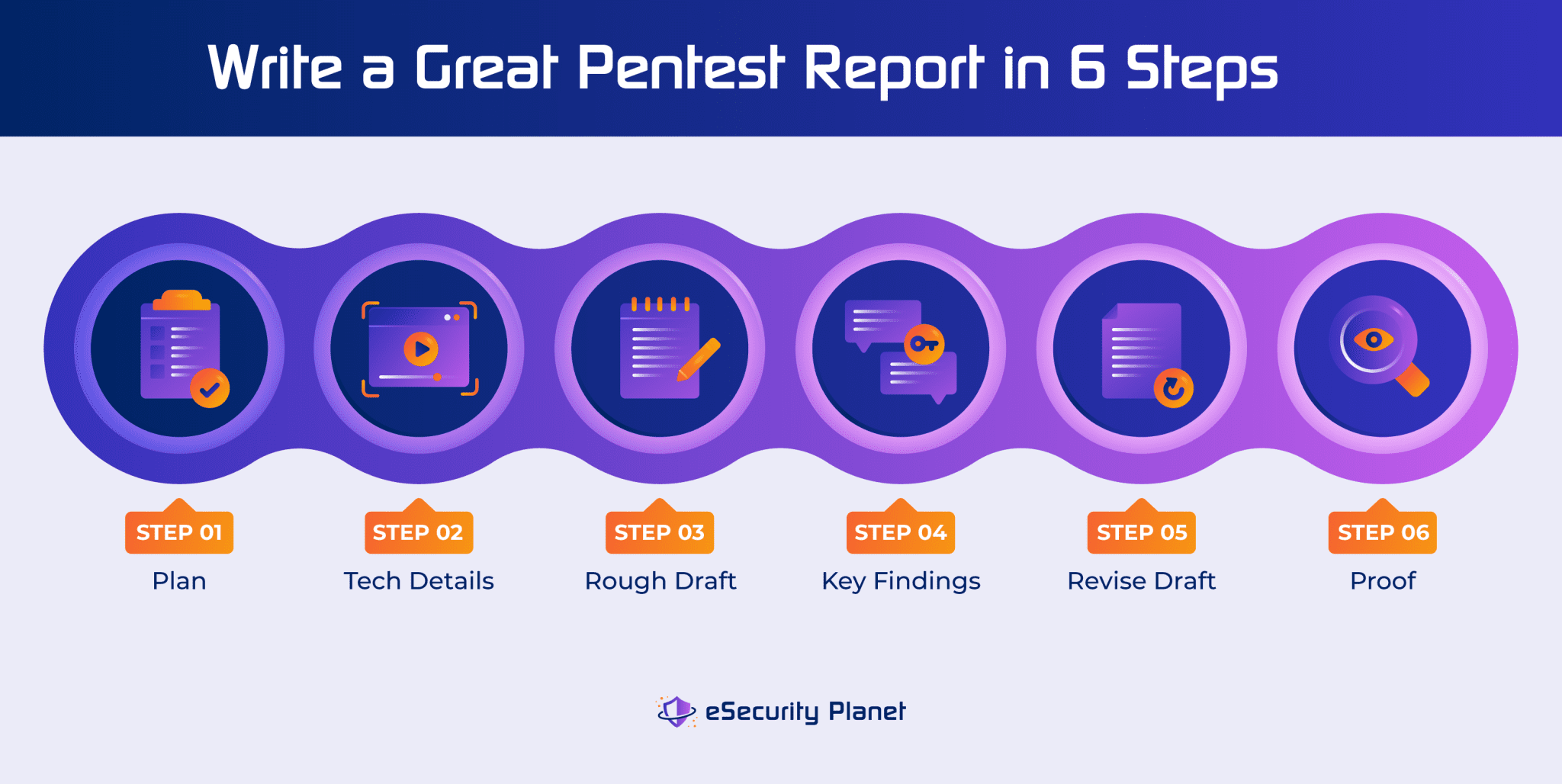
How to Write a Pentesting Report With Checklist
Pentesting Report Template
Editable Test Report Template
Pentest Report Template Word
Test Report Template prntbl.concejomunicipaldechinu.gov.co
Sample Pentesting Report
What Does A Testing Report Look Like?
What To Expect From A Testing Report?
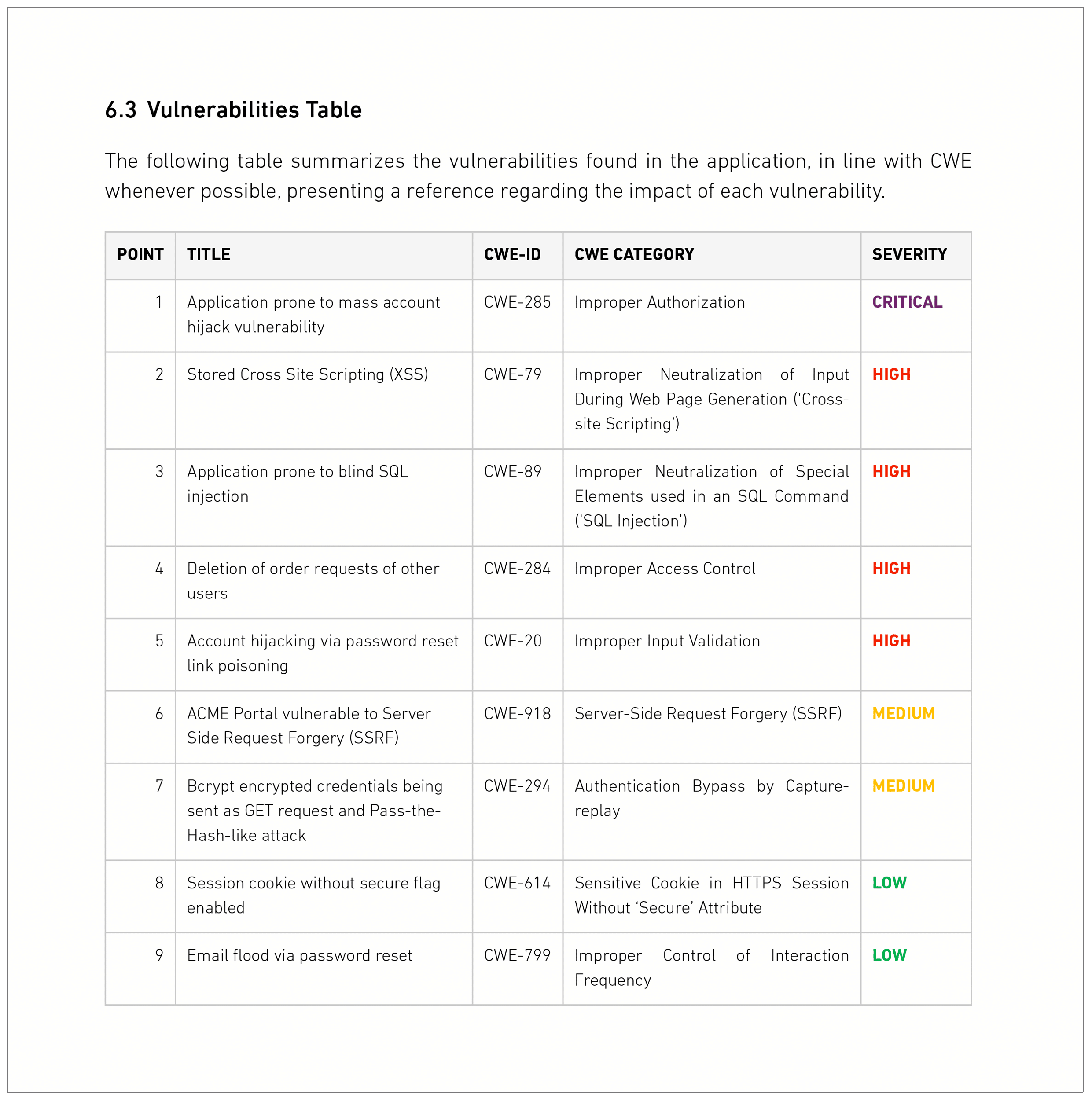
Pentesting Report PDF Vulnerability Test
Enhance Your Security Posture With Cobalt's Fast And Scalable Penetration Testing Services, Backed By A Team Of 450+ Experts To Identify And Remediate Vulnerabilities Effectively.
They Can Examine Whether A System Is Robust Enough To Withstand Attacks From Authenticated And.
In Most Cases, Both Humans And Automated.
These Vulnerabilities May Exist In Operating Systems,.
Related Post: